Blind Infection 1
- Author
- Battlemonger
- Category
-
Forensics - Points
- 470
- Solves
- 23
- Files
- chall.zip
- Flag
-
SEKAI{R3m3b3r_k1Dz_@lway5_84cKUp}
Investigator: It looks like your files were encrypted — do you have a backup?
Me: Online, yes, but even the backup links got encrypted. Can you help me find anything?
Warning
Warning: This payload contains ransomware. Consider using a fresh virtual machine, as you may risk losing your data. Although surface analysis is safe (and the ransomware is user-triggered), proceed with caution.
Reconnaissance
$ tree.├── etc├── home├── root└── snapUnzipping the provided .zip provides us with four Linux directories: etc/, home/, root/, and snap/. Let’s start off with a little bit of reconnaissance.
A good habit with these types of challenges is to check etc/passwd, a list of system accounts. If we grep for those with root permission, we find that the user sekaictf was a superuser:
$ cat etc/passwd | grep 'bash'root:x:0:0:root:/root:/bin/bashsekaictf:x:1000:1000:sekaictf,,,:/home/sekaictf:/bin/bashAlthough it isn’t necessarily pertinent to the challenge, make sure you check home/sekaictf/.bash_history alongside grep -r "SEKAI{ - they can be pretty handy sometimes!
Document Recovery
Next, we’ll look for user files. The Documents/ and Pictures/ folder of the sekaictf user has them, but everything seems to be encrypted with no indication of the encryption method used.
The description talks about having a backup for the encrypted files in the form of links, meaning we should be looking for browser-related content (i.e. search history). Ubuntu 22 stores Firefox as a SnapCraft app in snap/ by default — we can also grep for the term 'firefox' for its location:
home/sekaictf$ tree | grep -C 5 firefox│ ├── german.png│ ├── ginger.png│ └── meme.png├── Public├── snap│ ├── firefox│ │ ├── 1551│ │ ├── 1589│ │ ├── common│ │ └── current│ └── snapd-desktop-integrationFirefox is located in home/sekaictf/snap/firefox/, while the profile information of the user is located at firefox/common/.mozilla/firefox/p3zapakd.default/. p3zapakd is the name of the user.
Firefox stores your visit history in the places.sqlite SQLite database (read more about how Firefox stores your information here). You can use an online tool or sqlite3 to view it! The table we need is moz_places, which is a hefty piece of work with more than 750+ URLs:
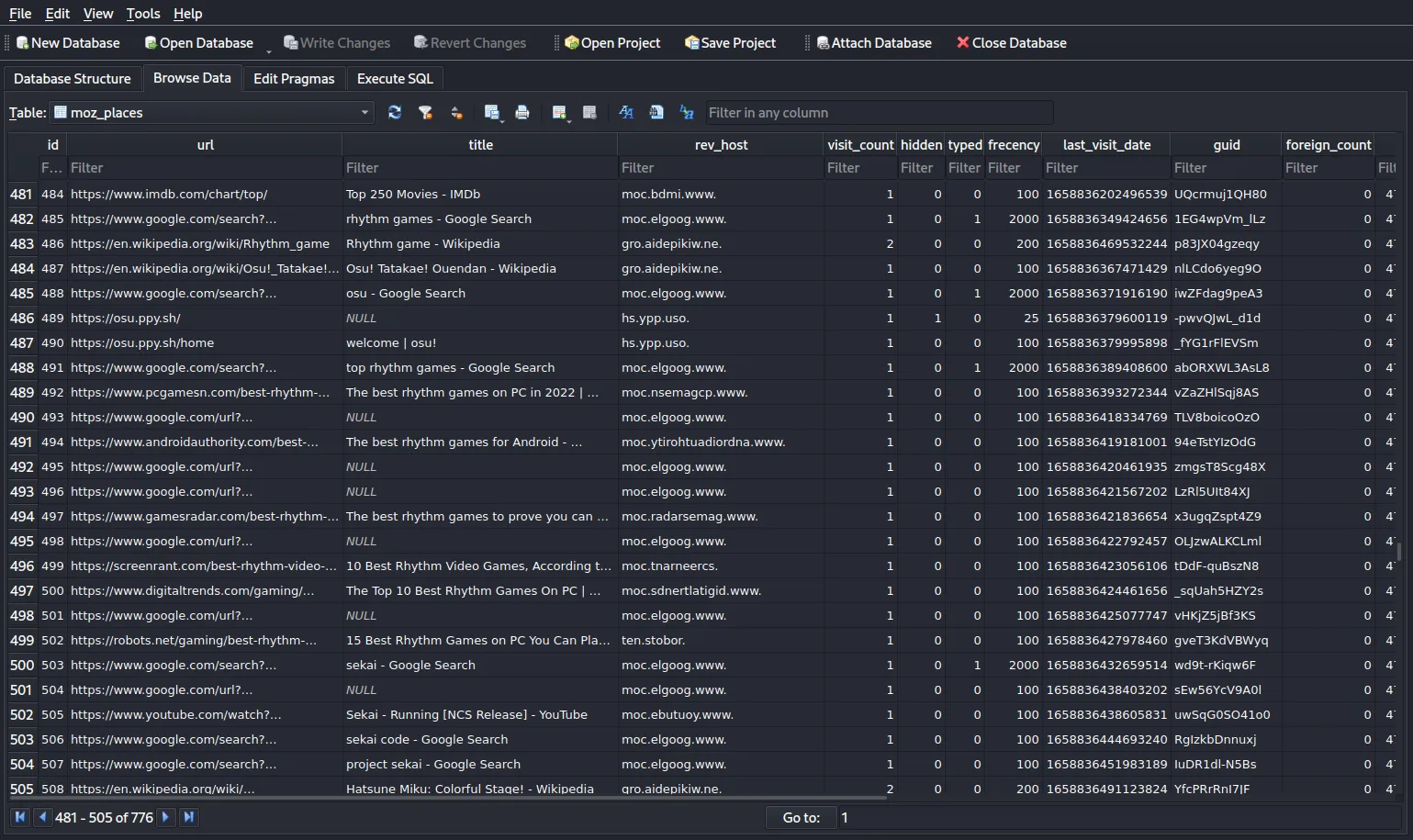
Yes, it’s super meticulous, but a true forensics investigator would champ it through! Scrolling through the table, we notice that the user follows a certain trend, as following:
- The user searches about a topic on Google
- The user visits that appear in the search results
- The user visits the URL https://paste.c-net.org with a subdirectory consisting of two random words (possibly to bookmark them for later)
Visiting any of these pastes and recognizing that the content should be the same as encrypted files in the Documents/ folder is key to Part 1. This is further facilitated by the fact that names of the encrypted files in Documents/ are very descriptive:
home/sekaictf/Documents$ lsaes.txt ippsec.txt python.txt warandpeace12.txtassignment.txt jokes.txt roblox.txt warandpeace13.txtbillionaires.txt joke.txt robomagellan.txt warandpeace14.txtbrainteasers.txt jsinterview.txt rsa.txt warandpeace15.txtcountries.txt juggle.txt science.txt warandpeace1.txtctfwins.txt katana.txt sekai.txt warandpeace2.txtelements.txt leetcode.txt shakespeare.txt warandpeace3.txtexcuses.txt loi.txt song.txt warandpeace4.txtflag.txt maths.txt sql.txt warandpeace5.txtfortnite.txt oscp.txt tools.txt warandpeace6.txtginger.txt overflow.txt volatility.txt warandpeace7.txtgirlfriend.txt privesc.txt warandpeace10.txt warandpeace8.txtgraphql.txt program.txt warandpeace11.txt warandpeace9.txtInstinctively, we would want to visit all these pastes.
There are 50 instances of the URL https://paste.c-net.org in the table and visiting them one-by-one isn’t very 1337 h4xx0r. We can execute some simple SQL on the table to extract all instances:
SELECT url FROM 'moz_places' WHERE URL like '%paste%'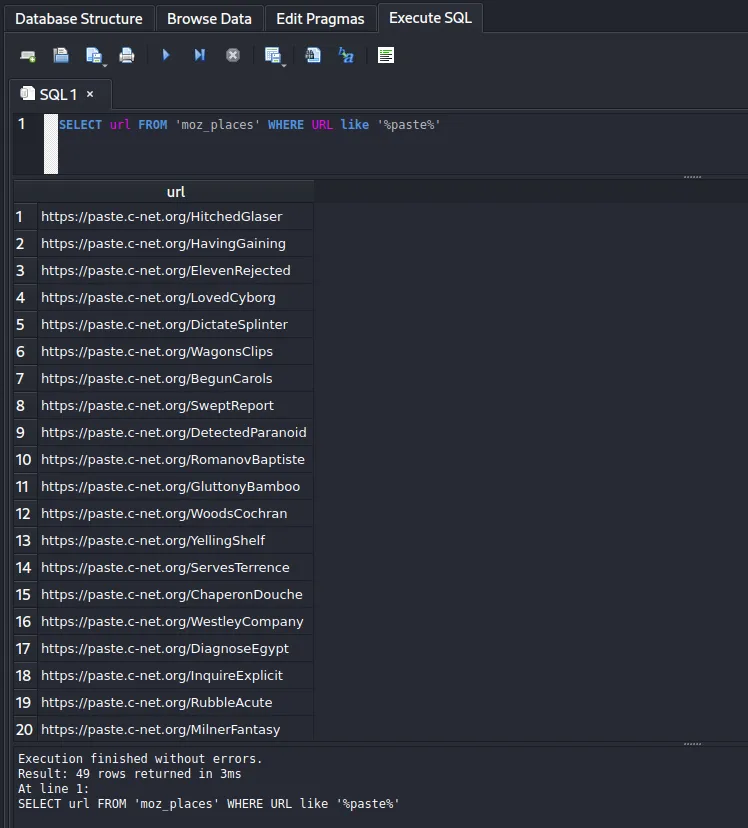
Let’s write a simple curl script with Python:
import requests
urls = [ "https://paste.c-net.org/HitchedGlaser", "https://paste.c-net.org/HavingGaining", "https://paste.c-net.org/ElevenRejected", "https://paste.c-net.org/LovedCyborg", "https://paste.c-net.org/DictateSplinter", "https://paste.c-net.org/WagonsClips", "https://paste.c-net.org/BegunCarols", "https://paste.c-net.org/SweptReport", "https://paste.c-net.org/DetectedParanoid", "https://paste.c-net.org/RomanovBaptiste", "https://paste.c-net.org/GluttonyBamboo", "https://paste.c-net.org/WoodsCochran", "https://paste.c-net.org/YellingShelf", "https://paste.c-net.org/ServesTerrence", "https://paste.c-net.org/ChaperonDouche", "https://paste.c-net.org/WestleyCompany", "https://paste.c-net.org/DiagnoseEgypt", "https://paste.c-net.org/InquireExplicit", "https://paste.c-net.org/RubbleAcute", "https://paste.c-net.org/MilnerFantasy", "https://paste.c-net.org/ArticleOutdoors", "https://paste.c-net.org/DigitAccosted", "https://paste.c-net.org/DaylightMaguire", "https://paste.c-net.org/GaugeComposed", "https://paste.c-net.org/OlympusSeminar", "https://paste.c-net.org/LackeysEternity", "https://paste.c-net.org/CoachedBarks", "https://paste.c-net.org/StungFarted", "https://paste.c-net.org/BlisterQuebec", "https://paste.c-net.org/BiancaShanghai", "https://paste.c-net.org/ReboundStopping", "https://paste.c-net.org/EmptyPaste", "https://paste.c-net.org/ToursForks", "https://paste.c-net.org/GuineaShovel", "https://paste.c-net.org/LettinAverage", "https://paste.c-net.org/CuveeBouncer", "https://paste.c-net.org/CraziesCritique", "https://paste.c-net.org/QuitterTasks", "https://paste.c-net.org/MashburnEdmund", "https://paste.c-net.org/PollsFenwick", "https://paste.c-net.org/FillsTaunt", "https://paste.c-net.org/RussiansEstimate", "https://paste.c-net.org/HughesRecant", "https://paste.c-net.org/CelloFilmed", "https://paste.c-net.org/CrushMalcolm", "https://paste.c-net.org/ProphecyWestside", "https://paste.c-net.org/GardenOccur", "https://paste.c-net.org/QuittingPeterson", "https://paste.c-net.org/BainesPouty",]
for url in urls: r = requests.get(url) if "SEKAI{" in r.text: print(r.text)Running the script:
$ python3 solve.pySEKAI{R3m3b3r_k1Dz_@lway5_84cKUp}